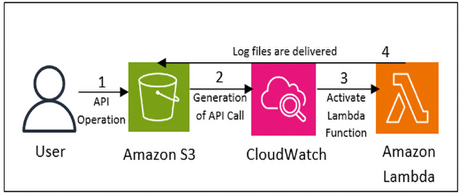
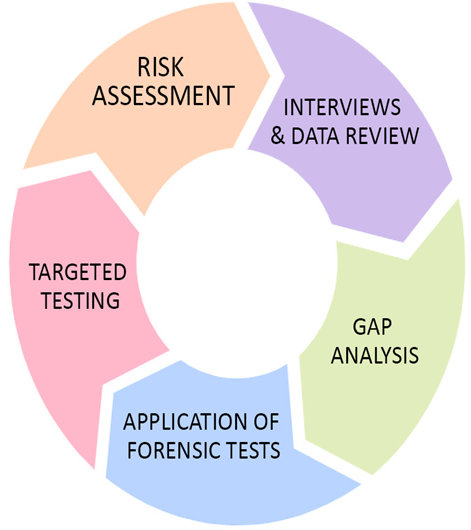
Creating a unified monitoring solution – Operating and Monitoring IoT Networks
Creating a unified monitoring solution for an IoT network that includes both on-premises and cloud-based resources can be challenging, but is essential for ensuring comprehensive visibility and control over the entire network. Fortunately, AWS provides a range of tools and services that can be used to create unified monitoring solutions for IoT networks.
One key tool for creating a unified monitoring solution is AWS IoT SiteWise, which can collect, structure, and search IoT data from industrial equipment and processes across on-premises and cloud-based resources. SiteWise enables organizations to standardize and normalize data from disparate sources, making it easier to analyze and monitor the health and performance of entire networks.
Another important tool for creating a unified monitoring solution is AWS Systems Manager, a management service that enables an organization to automate operational tasks and manage on-premises and cloud-based resources from a single console. Systems Manager can be used to monitor system health and performance, track compliance with security and regulatory requirements, and automate responses to common issues.
To create a unified monitoring solution for IoT networks, organizations should first define their monitoring requirements and establish clear objectives and goals for the monitoring solution. They should also identify the KPIs that will be used to measure system performance and health and develop plans for monitoring those KPIs across all on-premises and cloud-based resources.
Organizations should leverage AWS CloudFormation or AWS Control Tower to automate the deployment and management of monitoring resources across both on-premises and cloud-based environments. CloudFormation enables organizations to create and manage a collection of related AWS resources, while Control Tower provides a pre-configured environment that includes best practices for security and compliance.
There are many tools that are used in conjunction with AWS to achieve such a centralized way of monitoring our resources. SIEM platforms, such as Splunk or IBM QRadar, offer this kind of integrated approach. They aggregate and analyze log data from various sources within the IoT ecosystem, helping in detecting, analyzing, and responding to security incidents and threats.
Finally, organizations should leverage dashboards and visualization tools, such as AWS QuickSight, to provide real-time visibility into system performance and health across on-premises and cloud-based resources. Dashboards can be customized to display relevant metrics and KPIs and can be shared with relevant stakeholders to ensure that everyone has a comprehensive view of system performance. By creating a unified monitoring solution for IoT networks, an organization can gain comprehensive visibility and control over its entire network, making it easier to detect and respond to potential issues before they become critical problems. An example of how such a solution has been utilized is with Philips. Philips has effectively harnessed the power of AWS to revolutionize its approach to healthcare technology. It has established a notable presence in the digital healthcare sphere with its HealthSuite Digital Platform, developed on AWS. This platform has been transformative in streamlining patient monitoring remotely, efficiently managing a range of devices through cloud connectivity, and unifying diverse healthcare data for more coherent analysis. This strategic move has not only sped up the introduction of new healthcare technologies but has also ensured adherence to critical security regulations.
Additionally, Philips has made significant strides in the field of medical imaging diagnostics by leveraging artificial intelligence (AI) and machine learning through AWS services. The HealthSuite specifically targets the complexities involved in medical imaging data analysis. It serves as a comprehensive platform that aggregates various forms of data, including patient records and readings from wearable technology. This integration, facilitated by AWS IoT Core and Amazon SageMaker, empowers Philips to handle a vast network of IoT devices and extract valuable insights for clinical use. These innovations by Philips are a testament to the importance of the power of having a unified monitoring solution in organizations and how much it contributes to growth.