Continuous operation of IoT systems – Operating and Monitoring IoT Networks-2
Early detection of issues: Continuous monitoring of IoT networks enables organizations to detect issues early and resolve them before they turn into major problems. This helps prevent system downtime, reduce maintenance costs, and enhance the overall system performance.
Improved system performance: Real-time monitoring of IoT networks can identify performance bottlenecks and help optimize the system for better performance. This leads to faster response times, improved system reliability, and enhanced user experience.
Better decision-making: IoT monitoring solutions provide real-time data and insights that can inform effective decision-making. Organizations can use the data to make informed decisions that improve operational efficiency, reduce costs, and enhance overall business performance.
Enhanced security: Continuous monitoring of IoT networks helps identify security vulnerabilities and potential threats. This enables an organization to take proactive measures to prevent attacks and protect sensitive data, ensuring the safety and security of the system.
Predictive maintenance: Continuous monitoring of IoT networks can identify patterns and trends that can inform predictive maintenance. This helps an organization identify potential failures before they occur, reducing maintenance costs and increasing the overall lifespan of the system.
Scalability: Continuous monitoring solutions can scale to meet the needs of expanding IoT networks. This enables an organization to handle large volumes of data and maintain a comprehensive view of the system’s performance, even as the network expands.
On the other hand, it is important to understand how the monitoring framework is done over AWS and in general. In Figure 9.1, we can see how this framework can be visualized and stepped through for our needs:
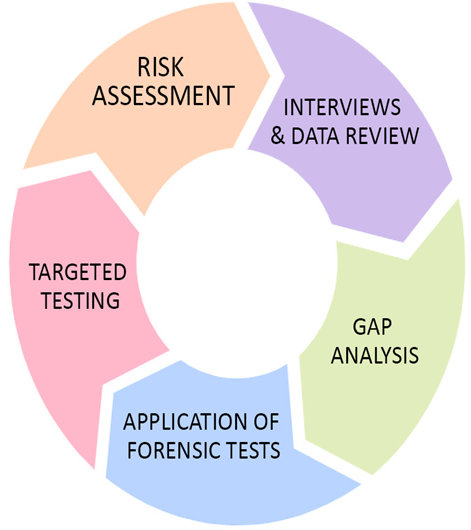
Figure 9.1 – IoT network monitoring framework
Here, we have the framework that we will walk through step by step to understand what each step encompasses:
Targeted testing: This step involves testing specific areas of the IoT network to identify potential vulnerabilities or weaknesses. Testing may involve performing a penetration test or using specialized tools to identify vulnerabilities in the network. In a smart home IoT network, targeted testing might involve using a network scanning tool such as Nmap to identify open ports on devices such as smart thermostats or security cameras.
Risk assessment: In this step, the results of the targeted testing are analyzed to identify potential risks and threats to the IoT network. A risk assessment helps to prioritize potential vulnerabilities based on their likelihood and potential impact on the network. After identifying vulnerabilities in the smart home network, a risk assessment could determine that an unpatched security camera poses a high risk due to its accessibility from the internet and the potential for it to be used as a gateway to access other devices on the network.
Interviews and data review: This step involves interviewing key stakeholders and reviewing data from various sources, such as system logs and incident reports. The goal is to gather additional information about potential vulnerabilities and risks to the IoT network. Interviews with the smart home’s residents could reveal that they are unaware of the need to regularly update device firmware. Reviewing system logs might show repeated attempts to access devices from unrecognized IP addresses, indicating potential security threats.
Gap analysis: This step involves comparing the results of the previous steps to the organization’s security policies and procedures. This helps to identify any gaps in the security posture of the IoT network and determine areas where improvements are needed. Comparing the current security measures of the smart home network with industry best practices might reveal gaps such as a lack of regular firmware updates, an absence of strong password policies, or a failure to segment the network to isolate critical devices from one another.
Application of forensic tests: The final step involves conducting forensic tests on the network to gather additional information about potential vulnerabilities and risks. Forensic tests may include analyzing system logs or performing a deep dive into specific areas of the network to identify potential issues. Forensic analysis of the smart home network could involve examining the security camera’s logs to trace back to the origin of unauthorized access attempts. It might also include a deep dive into network traffic to identify any unusual patterns that could indicate a breach or an ongoing attack.
By following these five steps, organizations can ensure that their IoT networks are monitored effectively and continuously, helping to minimize potential risks and threats and ensuring the overall security and efficiency of their networks.