Monitoring for security purposes – Operating and Monitoring IoT Networks
Monitoring IoT networks for security purposes is critical to ensure that the devices and data are protected from cyber threats. AWS offers a range of tools and services to help organizations monitor the security of their IoT networks.
One key tool for security monitoring on AWS is Amazon GuardDuty, a threat detection service that continuously monitors for malicious activity and unauthorized behavior across AWS accounts and workloads. GuardDuty can be used to detect and respond to potential security threats in real time and can alert relevant personnel when suspicious activity is detected.
Another important tool for security monitoring on AWS is AWS IoT Device Defender, a managed service that audits and monitors the security of IoT devices and applications. Device Defender can be used to detect and respond to security threats by monitoring device behavior, identifying anomalies, and triggering alerts when suspicious activity is detected.
AWS also offers a range of identity and access management (IAM) tools, including AWS IAM and AWS Single Sign-On (AWS SSO), which can be used to control and manage user access to IoT devices and data. IAM and SSO can be used to set permissions, enable multi-factor authentication, and enforce policies to ensure that only authorized personnel can access sensitive data.
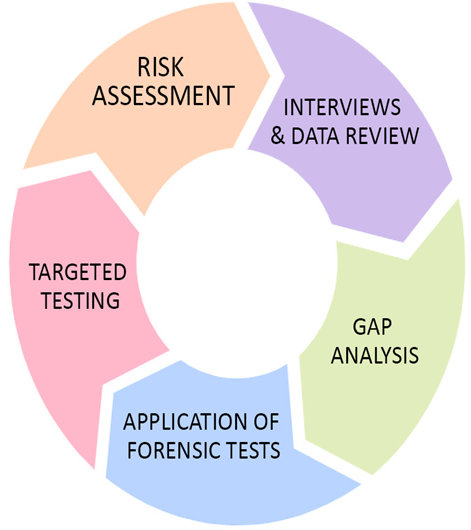
To implement an effective security monitoring solution on AWS for IoT networks, organizations should first identify their security requirements and establish key security metrics to measure system performance. They should also establish security policies and procedures to govern access control, vulnerability management, incident response, and other security-related activities.
Organizations should also leverage security monitoring tools and services, such as GuardDuty and Device Defender, to continuously monitor for security threats and vulnerabilities. They should regularly review and analyze security logs and audit trails to identify potential security issues and opportunities for improvement.
Outside of AWS, there are many solutions that help with monitoring IoT deployments as well. It starts with doing an analysis of network traffic. Tools such as Wireshark or tcpdump can be employed for packet sniffing and network traffic analysis, providing insights into potential malicious activities or unauthorized data transmission. In terms of mitigating risks, endpoint security solutions such as antivirus software, intrusion prevention systems (IPSs), or advanced threat protection (ATP) services can be used to safeguard IoT devices. These solutions help in identifying and mitigating malware, ransomware, and other forms of cyberattacks targeting IoT endpoints.
Finally, organizations should establish processes for continuous improvement, regularly reviewing and updating their security monitoring strategies to ensure that they remain effective and up-to-date. By continually refining their security monitoring strategies, organizations can ensure that their IoT networks remain secure and protected from cyber threats.