Technical requirements – Examining Security and Privacy in IoT
From smart homes to connected cars, IoT devices have become ubiquitous in our daily lives. However, with increased connectivity and data exchange comes the risk of security and privacy breaches. As more and more sensitive information is transmitted through these devices, it is essential to examine security and privacy measures in place to protect both the users and the devices themselves.
In this chapter, we will explore various security and privacy concerns in IoT, including risks associated with data breaches and strategies used to mitigate them. We will also discuss the importance of privacy in IoT and how it is protected, as well as the challenges of implementing security measures in a rapidly evolving technological landscape. By examining these critical issues, we can gain a better understanding of the measures needed to ensure the security and privacy of IoT devices and networks.
In this chapter, we’re going to cover the following main topics:
The current state of risk and security within IoT
Security and privacy controls within the cloud management landscape
Risk management within the IoT landscape
Privacy and compliance within IoT networks
Cryptography controls for the IoT landscape
Practical – Creating a secure smart lock system
Technical requirements
This chapter will require you to have the following hardware and software installed:
Hardware:
- Raspberry Pi
- Single-channel relay
- 1 1k Ohm resistor
- Push button switch
- Jumper cables
- Breadboard
- Mobile charger 5V/1A to use as power supply
Software:
- Blynk app
- Arduino IDE
You can access the GitHub folder for the code that is used in this chapter at https://github.com/PacktPublishing/IoT-Made-Easy-for-Beginners/tree/main/Chapter11/.
The current state of risk and security within IoT
As IoT technology continues to evolve and expand into new areas of our lives, it is critical that we understand the current state of risk and security within IoT networks. In this section, we will explore the current landscape of IoT security, including the most common types of IoT security threats and the current state of IoT security standards and regulations. We will also discuss best practices for securing IoT networks and devices, as well as challenges and opportunities for improving IoT security in the future. We can start off by taking a look at how security encompasses IoT in Figure 11.1:
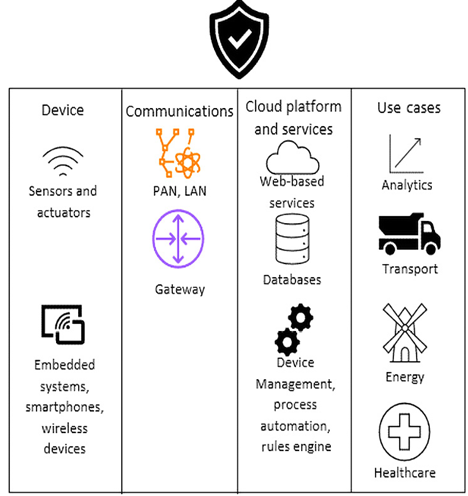
Figure 11.1 – Overview of how security encompasses IoT
Figure 11.1 presents a structured overview of the current state of risk and security within IoT. The diagram is segmented into four main columns, representing distinct aspects of IoT: Device, Communications, Cloud platform and services, and Use Cases.
The diagram emphasizes the diverse facets of IoT, spanning from device-level hardware to broad use cases. It shows expansive areas where security is paramount in the IoT ecosystem, from individual devices and their communication pathways to the cloud platforms that store and process data, and finally, the real-world applications and sectors that implement IoT solutions.
We can continue the discussion by taking a look at challenges within security on IoT networks.